Tuesdays are when Microsoft publishes patches to their software, and today they’ve published quite a few (if you use Windows then you should be installing the patches today).
However today there’s a malicious email being sent around that looks like it came from Microsoft (it’s actually fake). The email tells people about the patches and has a file attached.
The attachment isn’t really a Microsoft update, it’s actually a trojan that installs something on your PC that lets hackers log into it, without you ever finding out. You really don’t want this kind of thing installed on your PC.
The email has a few features designed to convince people that it’s genuine, such as a PGP signature at the end, and the fake sender address.
The subject of the email is:
Security Update for OS Microsoft Windows
If you see this just delete it. You should also have a good spam filter for your inbox – email services such as Gmail do a good job of this. For businesses it’s a little more complicated and even more important. You should also invest in a good antivirus package, one that checks everything and downloads updates at least once a day.
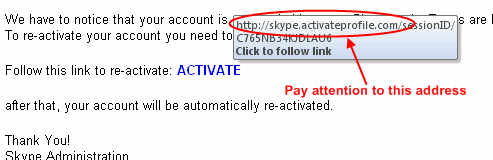
And remember to never trust attachments you unexpectadly receive(you didn’t ask Microsoft to send you an attachment, so why would they really do this?)
 Yahoo owns some technology called DomainKeys that can verify the sender of some emails. One thing it can do is recognise real and fake emails from eBay and PayPal. This is good because quite a few phishing emails claim to be from eBay or PayPal, intended to trick people into providing their login details.
Yahoo owns some technology called DomainKeys that can verify the sender of some emails. One thing it can do is recognise real and fake emails from eBay and PayPal. This is good because quite a few phishing emails claim to be from eBay or PayPal, intended to trick people into providing their login details.