 If you carry a notebook outside of your home or office then Whole Disk Encryption is a technology you should be interested in. It’s also called Full Disk Encryption. First let’s identify the problem.
If you carry a notebook outside of your home or office then Whole Disk Encryption is a technology you should be interested in. It’s also called Full Disk Encryption. First let’s identify the problem.
Most people who carry notebook computers (laptops) keep sensitive files on the machine’s drive. Business documents, business databases, contact lists, emails, chat logs, password lists, etc. The most common situation is someone carrying confidential documents on the computer.
If the notebook is lost or stolen then whoever holds the notebook computer has access to the files. Login passwords aren’t enough to protect the documents, they’re easily recovered by anyone.
A more worrying trend is for international business travellers who carry confidential data on their notebooks.  There have been many instances of airport customs staff not only inspecting the notebook for banned items but they’re now looking in the notebook’s hard drive and looking through any documents stored there. Their excuse is that they have to search for anything that’s a threat to national security. Irrespective of why they’re doing this the point is that someone else can gain access to your files at airports. Read this article for an example. And for examples of lost or stolen notebooks see here.
There have been many instances of airport customs staff not only inspecting the notebook for banned items but they’re now looking in the notebook’s hard drive and looking through any documents stored there. Their excuse is that they have to search for anything that’s a threat to national security. Irrespective of why they’re doing this the point is that someone else can gain access to your files at airports. Read this article for an example. And for examples of lost or stolen notebooks see here.
Most large companies are now telling their staff to wipe all documents off notebook computers before travelling. This is excellent advice.
Another solution is to use whole disk encryption. This is a software technology that encodes the entire drive so that it’s unreadable without a password. At present this technology is rarely used on notebooks.
Advantages:
- It’s not possible for someone to extract files from a lost or stolen notebook computer
- You don’t have to remember to turn it on or to prepare anything before you leave home or the office. It’s always enabled
Disadvantages:
- Not all encryption programs are free (read below for some good news on free software)
- It slows down the computer
- You have to enter another password before using the computer
- It doesn’t protect you from malware (trojans etc). You still need a good antivirus system
- You must have a backup of all your data at home or at the office. If something goes wrong with the computer then there’s no way to recover the data without a backup
- Security is only as good as your password. If you use your car number plate or some other easy to guess password then it’s not really secure. You need to use a good password.
 So with more disadvantages than advantages you’re probably put off. It depends how valuable your files are. If you’re a lawyer carrying around all your client’s documents then your files are probably quite valuable, and you should be doing everything in your power to stop strangers getting at them.
So with more disadvantages than advantages you’re probably put off. It depends how valuable your files are. If you’re a lawyer carrying around all your client’s documents then your files are probably quite valuable, and you should be doing everything in your power to stop strangers getting at them.
How does it work?
The technical explanations are beyond the scope of this article. It’s enough to know that it encrypts all of the drive. Older encryption programs encrypt some files only and smart hackers can usually recover all or part of documents. Therefore the “whole disk” part of the encryption program is important. The disk is completely unreadable and unusable without the password.
What whole disk encryption programs are available?
Recently there has been some progress on this and there are now good free versions including ones for Mac notebooks, as well as commercial solutions.
Free Windows Solutions:
There are quite a few solutions, below are the more popular ones available today.
- BitLocker – it comes with Windows Vista Enterprise, Windows Vista Ultimate, and Windows Server 2008
- TrueCrypt – a popular open source solution (see notes below). Available for Windows, Mac and Linux.
Commercial Solutions:
Below are low cost commercial solutions. There are many expensive enterprise level solutions not listed here.
- PGP – This program has been around for a very long time and is trusted by many people and companies. On the 13th Feb 2008 a version was also made for Apple Macs.
Summary
If you take your computer outside of a secure environment (home, office, etc) and you have anything on there you wouldn’t like others to have then whole disk encryption is a must.
As for airport customs and other law enforcement agencies, a lot of countries have laws making it possible for them to demand your password. So while you can keep random strangers from reading your data it’s really up to you how you comply with legal requests to hand over data. At least you have a choice.
Notes:
Open Source: in security it’s often a good thing to make programs or algorithms open source. It enables the programming community or security community to review the code and find any possible bugs as quickly as possible. It’s also a form of full disclosure. With commercial solutions you have to trust a company that they didn’t include a backdoor for whatever reason. With open source solutions everything’s exposed for public review.
 If you’re curious then the following information could interest you 😉
If you’re curious then the following information could interest you 😉 In the security world AES is a recognised and trusted encryption protocol, so at first glance this external hard drive enclosure seems useful for transporting data outside the office or home.
In the security world AES is a recognised and trusted encryption protocol, so at first glance this external hard drive enclosure seems useful for transporting data outside the office or home. But they’ve recently barred high profile people, including MPs, celebrities and the Royal Family, from using the same online system for security reasons.
But they’ve recently barred high profile people, including MPs, celebrities and the Royal Family, from using the same online system for security reasons. If you carry a notebook outside of your home or office then Whole Disk Encryption is a technology you should be interested in. It’s also called Full Disk Encryption. First let’s identify the problem.
If you carry a notebook outside of your home or office then Whole Disk Encryption is a technology you should be interested in. It’s also called Full Disk Encryption. First let’s identify the problem. There have been many instances of airport customs staff not only inspecting the notebook for banned items but they’re now looking in the notebook’s hard drive and looking through any documents stored there. Their excuse is that they have to search for anything that’s a threat to national security. Irrespective of why they’re doing this the point is that someone else can gain access to your files at airports.
There have been many instances of airport customs staff not only inspecting the notebook for banned items but they’re now looking in the notebook’s hard drive and looking through any documents stored there. Their excuse is that they have to search for anything that’s a threat to national security. Irrespective of why they’re doing this the point is that someone else can gain access to your files at airports.  So with more disadvantages than advantages you’re probably put off. It depends how valuable your files are. If you’re a lawyer carrying around all your client’s documents then your files are probably quite valuable, and you should be doing everything in your power to stop strangers getting at them.
So with more disadvantages than advantages you’re probably put off. It depends how valuable your files are. If you’re a lawyer carrying around all your client’s documents then your files are probably quite valuable, and you should be doing everything in your power to stop strangers getting at them.
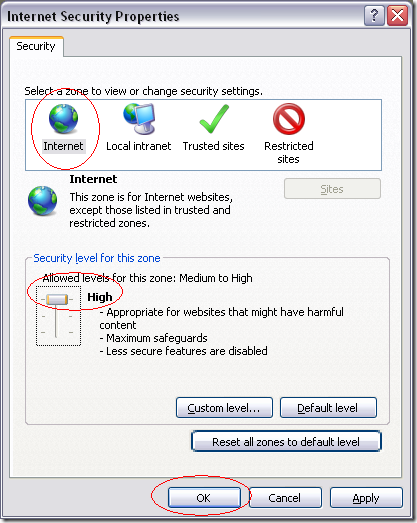
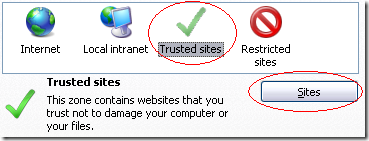
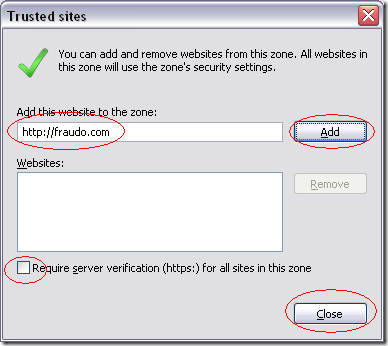
 The web site looks nice, contains a blog, a news section, and reviews. The authors went to some effort to make it look convincing. Most of the links on the site even work. It would be difficult to tell that this site will compromise your computer.
The web site looks nice, contains a blog, a news section, and reviews. The authors went to some effort to make it look convincing. Most of the links on the site even work. It would be difficult to tell that this site will compromise your computer.