DNS poisoning is an attack that’s becoming more widespread and it can affect most people using broadband.
Here’s a summary on what it is, how it can affect you, and what you can do about it.
Every time you use anything on the internet, including reading web pages, reading or sending emails, online chatting, etc, you use domain names (even if you don’t realise you’re using them). Domain names could be www.google.com, or www.fraudo.com, etc. They’re just addresses on the internet.
Your internet service provider (ISP) would have a machine in their network that your computer uses to look up these addresses. You won’t realise you’re using it but your computer definitely needs it (and it’s called a DNS server).
A DNS server is a phone book of web addresses.
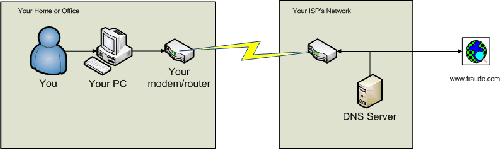
Here’s how things work on a healthy environment (click to enlarge):
You try to load up www.fraudo.com
- Your computer finds the DNS Server and asks it "where’s www.fraudo.com?"
- The DNS Server responds ("there it is –>")
- Your computer finds FraudO on the internet
All’s good and everyone’s happy browsing the internet. Along comes someone trying to hack your system. They make a change to your modem/router, telling it to use someone else’s DNS server.
How do they do this? The most common method today are viruses that break into routers and change settings. We’ll cover these another time.
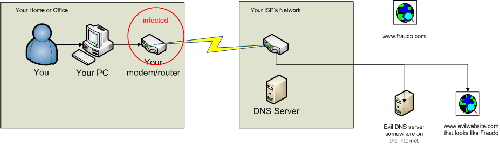
Here’s how an environment looks when it’s been DNS poisoned (click to enlarge):
Instead of using your ISP’s DNS server, it’s using a bad DNS server. The bad DNS server tells your computer how to find the evil websites instead of the real ones.
If this happens chances are you wouldn’t know how or why, it can be difficult to see what’s happening.
To prevent things like this happening here are some tips:
- Change the password on your router. Everyone knows the default password (here’s a list of all the default passwords, find yours in the list)
- Use a good virus scanner that scans all web pages, emails, and files
- Keep your virus scanner up to date

 The police were able to find him and arrest him. It’s important to secure your wireless networks so that other people don’t use it to commit crimes.
The police were able to find him and arrest him. It’s important to secure your wireless networks so that other people don’t use it to commit crimes. A quick update about online crime.
A quick update about online crime. It’s amazing how many new tactics these people come up with in order to steal your personal information. There’s a new “bot” that chats with users on Russian online chat rooms (a bot is a program that mimics a real person online). It’s called CyberLover and apparently it’s quite clever in impersonating a human and gets people talking to it.
It’s amazing how many new tactics these people come up with in order to steal your personal information. There’s a new “bot” that chats with users on Russian online chat rooms (a bot is a program that mimics a real person online). It’s called CyberLover and apparently it’s quite clever in impersonating a human and gets people talking to it. Some pages on the website gameige.com have been compromised, using iframes to cause people’s browsers to download malware and steal information from the computer. This is a risk if your web browser loads ActiveX controls (such as Internet Explorer). Gameige.com is used by players of online games such as World of Warcraft.
Some pages on the website gameige.com have been compromised, using iframes to cause people’s browsers to download malware and steal information from the computer. This is a risk if your web browser loads ActiveX controls (such as Internet Explorer). Gameige.com is used by players of online games such as World of Warcraft.