Vishing is short for voice phishing. This involves tricking someone into calling a phone number, listening to a recorded message, then being tricked into providing personal information to the phone service.
 Why would someone want to set this up? To collect your personal information, such as credit card number, its expiry date, your date of birth, PIN codes, etc. That information is then either sold on the black market or used by the scammers to steal or spend your money (this is also called identity theft).
Why would someone want to set this up? To collect your personal information, such as credit card number, its expiry date, your date of birth, PIN codes, etc. That information is then either sold on the black market or used by the scammers to steal or spend your money (this is also called identity theft).
Setting up an automated phone system like the ones described here is fairly easy these days, and fairly cheap.
Do people fall for it? Oddly enough, yes. Hopefully by now everyone’s getting the message not to trust strange web sites on the internet. But less obvious methods such as automated phone services are easily forgotten.
Anti virus software can’t stop you making a phone call. And people can be more trusting of “old fashioned” technology such as phones.
How does it work in practice? Here’s a summary of a recent vishing attempt.
- Emails are sent in bulk to as many people as possible.
- The emails have forged headers to appear to come from service@irs.gov
- The email contains an important looking message. Note that it doesn’t have any links to click on, instead it gives a phone number.
- Internal Revenue Service Tax Refund
After the last annual calculations of your fiscal activity we have determined that you are eligible to receive a tax refund of $215.
Tax Refund Number: <number here> – Will Expire on <date here>
Attention!
Tax refunds can be sent only to VISA or Mastercard DEBIT CARDS.
To receive your tax refund please call the IRS Tax Refund Department at: 602-427-59x
Internal Revenue Service
The reader takes an interest because of the offer for free money (who wouldn’t!) and calls the number shown.
Because the email already warned people they need a VISA or Mastercard card to receive payment they would be more willing to provide the card’s details.
Tips to avoid this scam:
- A good anti virus package will detect fraudulent emails such as the one above and filter them out, so invest in one if you haven’t already.
- In a company (small or large) invest in mail filtering. This is usually not included in corporate anti virus software.
- Think carefully why you received this email. Did you really lodge a tax submit a tax return recently, and in the country the email says it’s from? (e.g., if you live in USA and receive an email offering a tax refund from Australia, it’s most probably a scam).
- Does your country’s tax department even have your email address? If you didn’t give it to them then why are you receiving this email?
- Don’t blindly dial the number shown in the email. Look them up in your local phone book.
This isn’t limited to tax refunds. Other vishing variations may appear to be from banks or other financial institutions.
Another variation of this scam is to send people an SMS instead of an email, with a shorter version of the message above. Treat SMS’s like you would treat emails. Note: it’s also easy to forge SMS’s to appear to come from other people.
Automated voice systems can also initiate phone calls with fake caller IDs. The technology’s easily available. VoIP systems are even easier to set up.
The potential to trick people into handing over personal details is just as easy using phones as it is using emails and web pages.
 A new scam email is sent to people telling them they won a lottery. The email is full of interesting things to catch people’s attention such as a large dollar amount ($850,000) and social tricks such as asking them not to tell anyone about their winnings.
A new scam email is sent to people telling them they won a lottery. The email is full of interesting things to catch people’s attention such as a large dollar amount ($850,000) and social tricks such as asking them not to tell anyone about their winnings.
 This seems real enough but there’s one serious flaw. They include a link you can click on (where it says "Accept Friend"). Clicking on this link doesn’t take you to hi5’s web site, instead it takes you to a phishing site.
This seems real enough but there’s one serious flaw. They include a link you can click on (where it says "Accept Friend"). Clicking on this link doesn’t take you to hi5’s web site, instead it takes you to a phishing site. Microsoft’s Internet Explorer (IE) is very popular. Not long ago almost everyone used IE, it comes setup with almost every new PC sold (Windows PCs). And malware writers targeted IE because they could attack a majority of users just by concentrating on exploiting one browser. You could call it tall poppy syndrome.
Microsoft’s Internet Explorer (IE) is very popular. Not long ago almost everyone used IE, it comes setup with almost every new PC sold (Windows PCs). And malware writers targeted IE because they could attack a majority of users just by concentrating on exploiting one browser. You could call it tall poppy syndrome. A flaw in a beta version of Facebook made it possible to see member birth dates, even those set to hide this information. Birth dates are often used to confirm someone’s identity. By having a full name and birth date it’s possible to phone up companies and ask for more private information (this is called Identity Theft).
A flaw in a beta version of Facebook made it possible to see member birth dates, even those set to hide this information. Birth dates are often used to confirm someone’s identity. By having a full name and birth date it’s possible to phone up companies and ask for more private information (this is called Identity Theft).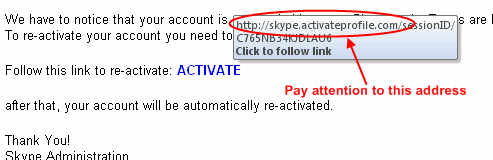
 Here’s a new spin in phishing attacks. The idea is to trick people into providing confidential data. This new technique is aimed at Gmail users. Here’s how it works:
Here’s a new spin in phishing attacks. The idea is to trick people into providing confidential data. This new technique is aimed at Gmail users. Here’s how it works: Why would someone want to set this up? To collect your personal information, such as credit card number, its expiry date, your date of birth, PIN codes, etc. That information is then either sold on the black market or used by the scammers to steal or spend your money (this is also called identity theft).
Why would someone want to set this up? To collect your personal information, such as credit card number, its expiry date, your date of birth, PIN codes, etc. That information is then either sold on the black market or used by the scammers to steal or spend your money (this is also called identity theft). The following are allowed to request your Tax File Number:
The following are allowed to request your Tax File Number: